




© S10 group 2025
+31 (0) 633 230 299
Live demos
A FREE, live RansomWare assessment test (POC)
Whitepapers
A ROI calculation
Additional information





St. Antoniuslaan 24 a
2171 EM Sassenheim
the Netherlands
+31(0)633 230 299



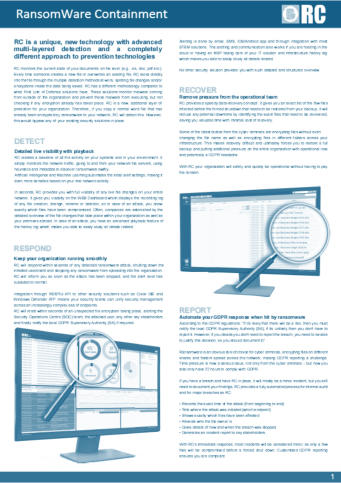
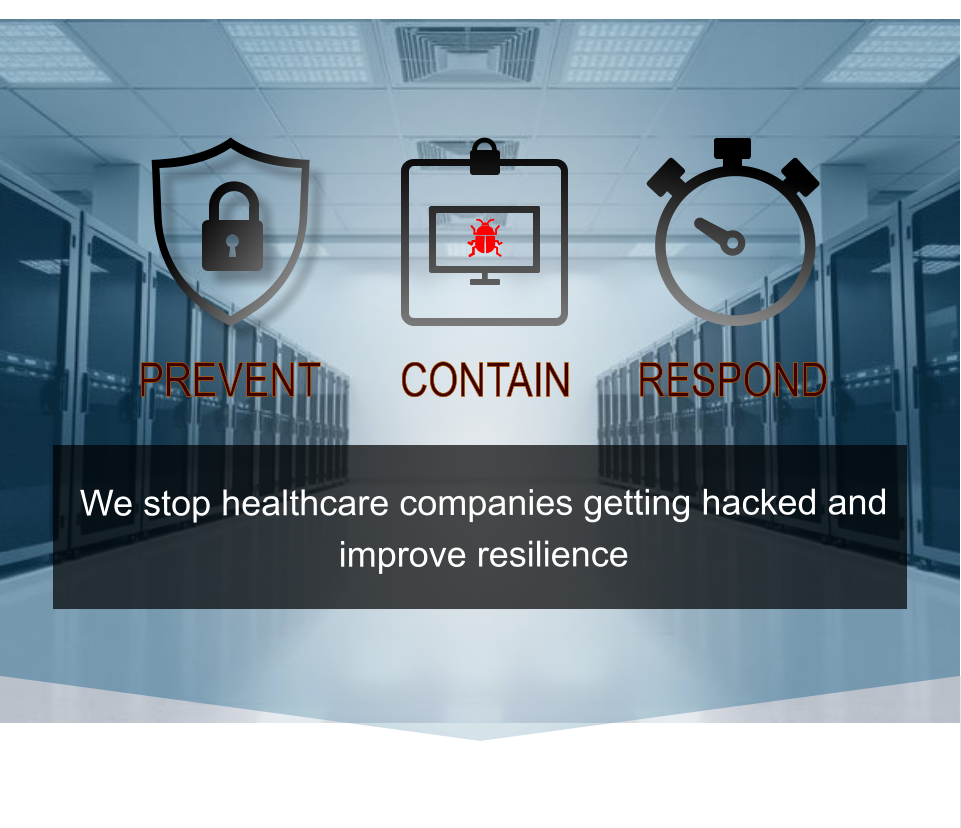
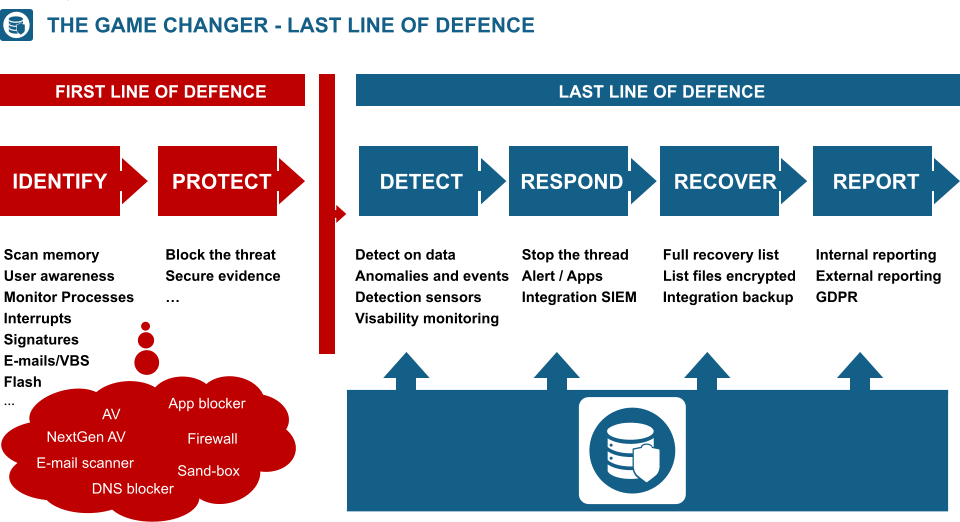
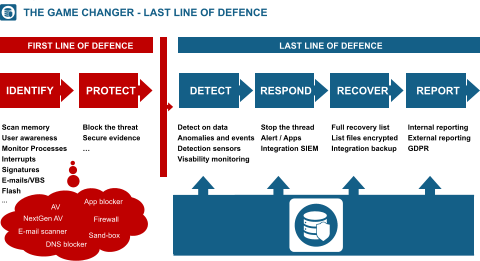
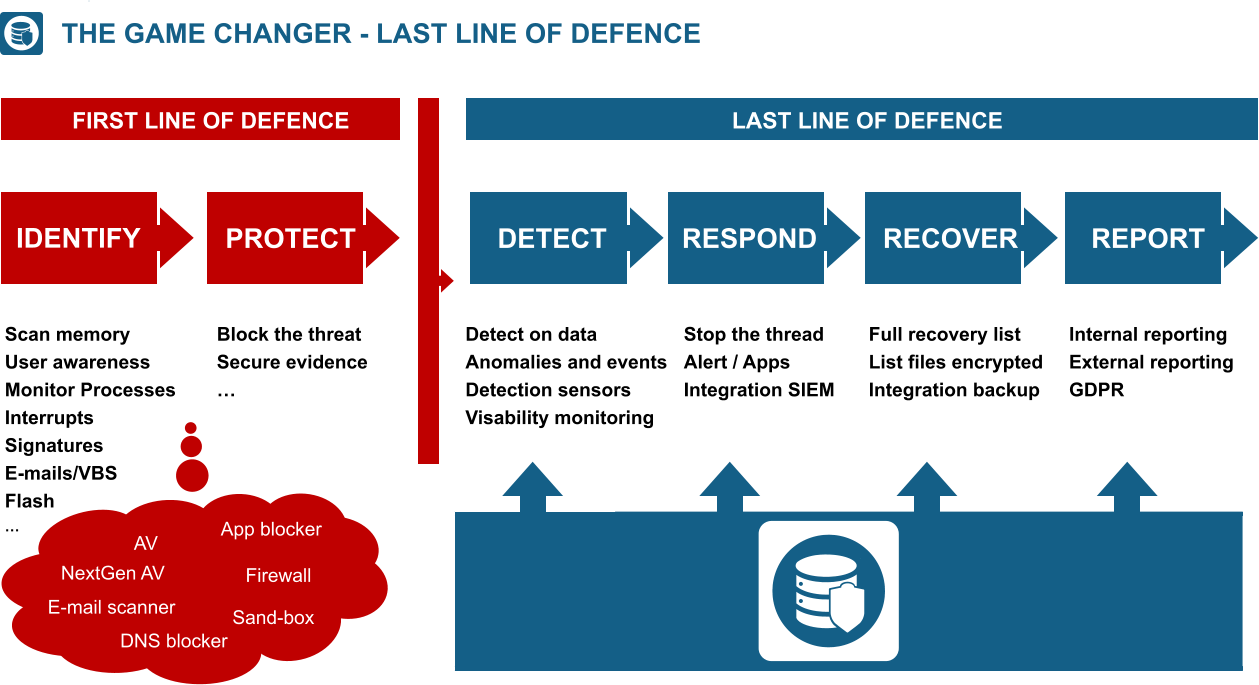
RansomWare containment


Contact us for:
Server intrusion protection





Prevent data exfiltration
Expose and trap invisible intruders on the
network
Secure remote server access
Prevent exploitation of admin privileges
Advanced monitoring and threat prevention
Contain breaches immediately
Reduce cyber insurance costs
and more…








Prevents downtime due to a RansomWare
encryption attack
Protects all critical IT infrastructure
Automated compliance reporting
Agentless & easy to implement
Isolates & quarantines
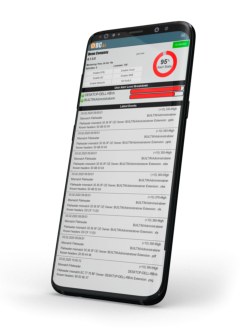
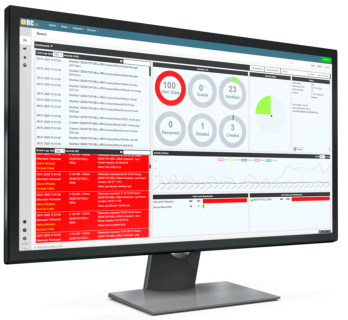
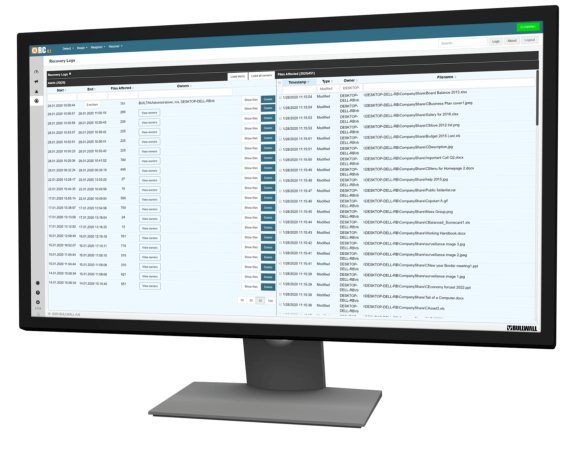
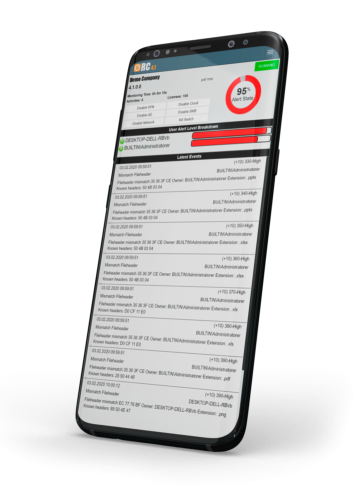
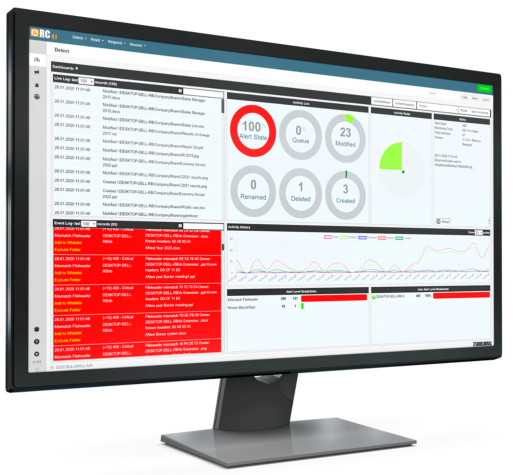
Detects, responds, recovers and reports
Integrates with SIEM, NAC, EDR and other
security solutions
And more...








Virtual server protection


Protect against access and encryption from
the outside
Entrap intruders attempting to remotely gain
access to servers
Detect and prevent malware deployment on
servers
Leverage 24/7 remediation of early indicators
of compromise
and more…






























































© S10 group 2025
+31 (0) 633 230 299

















St. Antoniuslaan 24 a
2171 EM Sassenheim
the Netherlands



+31(0)633 230 299





Contact us for:
Live demos
A FREE, live RansomWare
assessment test (POC)
Whitepapers
A ROI calculation
Additional information
Prevents downtime due to a RansomWare encryption attack
Protects all critical IT infrastructure
Automated compliance reporting
Agentless & easy to implement
Isolates & quarantines
Detects, responds, recovers and reports
Integrates with SIEM, NAC, EDR and other security solutions
And more...
RansomWare containment

Protect against access and encryption from the
outside
Entrap intruders attempting to remotely gain access
to servers
Detect and prevent malware deployment on servers
Leverage 24/7 remediation of early indicators of
compromise
and more…
Virtual server protection

Prevent data exfiltration
Expose and trap invisible intruders on the network
Secure remote server access
Prevent exploitation of admin privileges
Advanced monitoring and threat prevention
Contain breaches immediately
Reduce cyber insurance costs
and more…
Server intrusion protection


















© S10 group 2025
+31 (0) 633 230 299


St. Antoniuslaan 24 a
2171 EM Sassenheim
the Netherlands
+31(0)633 230 299



Contact us for:
Live demos
A FREE, live RansomWare
assessment test (POC)
Whitepapers
A ROI calculation
Additional information
Server intrusion protection


Prevent data exfiltration
Expose and trap invisible intruders on the network
Secure remote server access
Prevent exploitation of admin privileges
Advanced monitoring and threat prevention
Contain breaches immediately
Reduce cyber insurance costs
and more…










Virtual server protection


Protect against access and
encryption from the outside
Entrap intruders attempting to
remotely gain access to
servers
Detect and prevent malware
deployment on servers
Leverage 24/7 remediation of
early indicators of
compromise
and more…





RansomWare containment


Prevents downtime due to a RansomWare encryption attack
Protects all critical IT infrastructure
Automated compliance reporting
Agentless & easy to implement
Isolates & quarantines
Detects, responds, recovers and reports
Integrates with SIEM, NAC, EDR and other security solutions
And more...